Forensic challenges
Currently there are at least 2 Forensic challenges in which Xplico can be used and can facilitate the analysis. These two challenges are:
We do not answer the questions, here we will give some indication of use of Xplico.
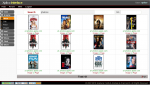
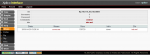
The “Ann’s AppleTV” pcap file has no particular problems of decoding, in fact if you process the pcap you obtain the data represented in the two pictures below.
For the “Forensic Challenge 2010 – pcap attack trace” pcap decoding requires more attention. In fact this pcap file has corrupted packet (and not retransmitted), so you must disable the Xplico checksum verification (HowTo).
From cli the command is:
./xplico -c config/xplico_cli_nc.cfg -m pcap -f attack-trace.pcap
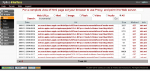
Since Xplico is able to recognize the protocols (not all) even if they use non-standard ports is easy to see what protocol was used and which data file was downloaded.
In the figure below there is the result of decoding with XI.
Enjoy ;).